
What Is [Security]?
Overview
Display the required information and configure various settings concerning the security of the Image Controller.
Setting Items
Screen access
Web Connection - [Security]
Setting item | Description |
|---|---|
Configure various settings related to the certificate. | |
Configure the setting to verify the certificate. | |
Set the time required to automatically log out when no operation is performed for the specified time after login to Web Connection. | |
When connecting the Image Controller to the network, you can ensure a certain level of security even if you do not have specialized knowledge of security. | |
Configure the setting to restrict displaying of personal information such as the user name or address. | |
Delete the jobs stored on the Image Controller. | |
Configure settings for accumulating job information processed on the system as log information. | |
Configure the settings to verify whether firmware is falsified. | |
Configure the setting to prevent a user other than the job owner from operating or deleting a job. | |
Configure the settings related to logs (audit logs) in which operations of this system are recorded. |
What is the Certificate?
Registering the certificate in the Image Controller allows you to encrypt communications between the Image Controller and the computer using SSL.
The Image Controller manages multiple certificates, enabling you to use them depending on protocols.
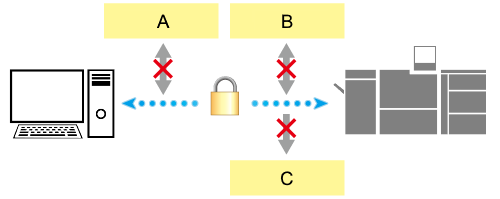
A: Prohibits spoofing.
B: Prohibits tampering.
C: Prohibits interception.
Create a new self-signed certificate, or install the certificate issued from the certificate authority (CA).
The table below shows the methods to use the certificate in the Image Controller.
Usage | Description |
|---|---|
Using the self-signed certificate | Create a certificate on the Image Controller. This method does not require the CA, so you can only enter the information required to create a certificate, and use the certificate. However, the security level is lower than the certificate issued from the CA. |
Using the certificate issued from the CA | Create certificate signing request data on the Image Controller, and request the trusted CA to issue the certificate of the Image Controller. After the examination by the CA, data is returned, so register the data in the Image Controller. |
 in the upper-right of a page, it turns into
in the upper-right of a page, it turns into  and is registered as a bookmark.
and is registered as a bookmark.