User's Guide
Using IPsec Communication
Configure the settings if IPsec is installed in your environment.
The IPsec technology prevents the falsification or leakage of data on the IP packet basis by using encryption technology. As IPsec encrypts data in the network layer, secure communication is ensured even if you use protocols in an upper layer or applications that do not support encryption.
- In the administrator mode, select [Network] - [TCP/IP Setting] - [IPsec] - [IPsec Setting], then click [OK].
- Click [Edit] from [IKEv1] or [IKEv2] in [IPsec Setting], then configure the following settings.
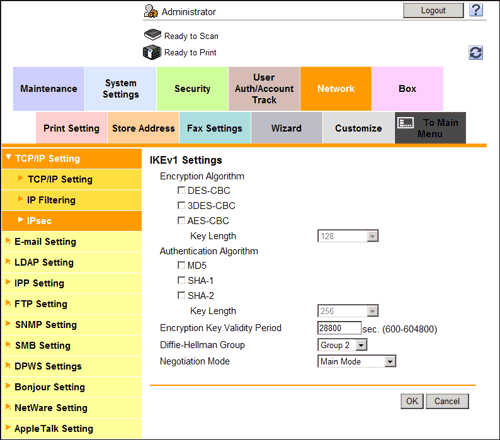
Settings Description [Encryption Algorithm]Select the encryption algorithm used for generating a common key used in communication.[Authentication Algorithm]Select the authentication algorithm used for generating a common key used in communication.[Encryption Key Validity Period]Enter a validation period of a common key used for encrypted communication.When this period has expired, a new key is created. This can secure the communication.[Diffie-Hellman Group]Select the Diffie-Hellman group.[Negotiation Mode]Select the method to securely generate a common key used for encrypted communication. - From [SA] in [IPsec Setting], click [Create] and register the Security Association (SA).
- Up to 10 groups can be registered for the SA.
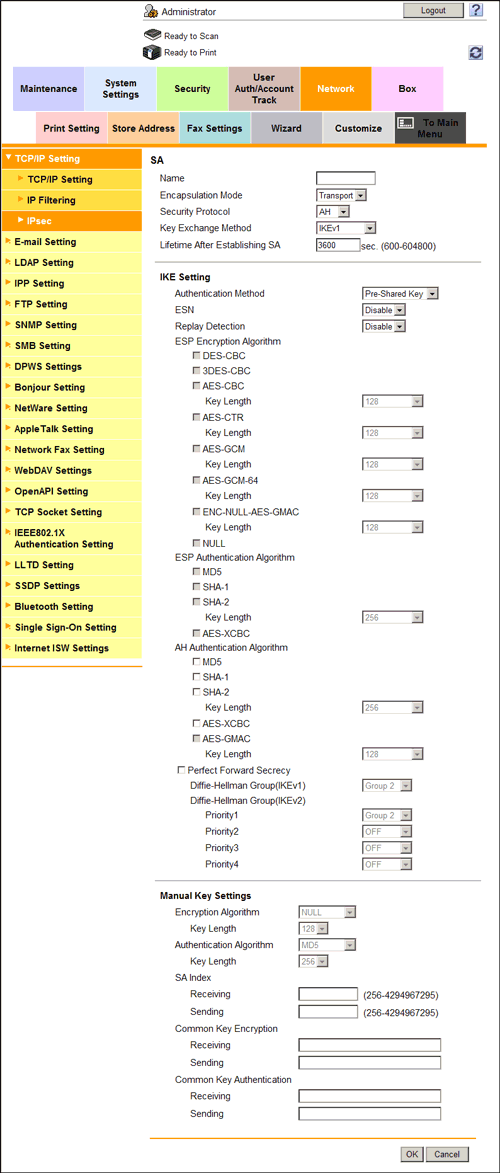
Settings Description [Name]Enter the SA name (1 to 10 characters).[Encapsulation Mode]Select an IPsec operation mode.[Security Protocol]Select a security protocol.[IKE Setting]Configure IKE settings used for this SA.[Authentication Method]Select an authentication method.[ESP Encryption Algorithm][Security Protocol][ESP], configure the ESP encryption algorithm.[ESP Authentication Algorithm][Security Protocol][ESP], configure the ESP authentication algorithm.[AH Authentication Algorithm][Security Protocol][AH], configure the AH authentication algorithm.[Perfect Forward Secrecy]Select this check box if you wish to increase the IKE strength.Selecting this check box increases the time spent for communication.[Diffie-Hellman Group(IKEv1)]/[Diffie-Hellman Group(IKEv2)]Select the Diffie-Hellman group.[Manual Key Settings]When using a device that does not support automatic key exchange using IKE, configure each parameter manually.[Encryption Algorithm]Select the algorithm to be used for encryption.[Authentication Algorithm]Select the algorithm to be used for authentication.[SA Index]Specify the SA Security Parameter Index to be added to the IPsec header.[Common Key Encryption ]Specify the common key used for encryption.You can specify different common keys respectively for send and receive.[Common Key Authentication]Specify the common key used for authentication.You can specify different common keys respectively for send and receive. - Up to 10 groups can be registered for the SA.
- From [Peer] in [IPsec Setting], click [Create] and register peers of this machine.
- You can register up to 10 peers.
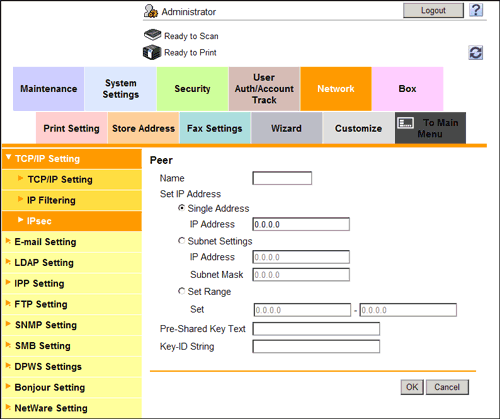
Settings Description [Name]Enter a peer name (1 to 10 characters).[Set IP Address]Specify the IP address of the peer.[Pre-Shared Key Text]Enter the Pre-Shared Key text to be shared with the peer (using up to 128 characters).Specify the same text as that for the peer.[Key-ID String]Enter the Key-ID to be specified for the Pre-Shared Key (using up to 128 characters). - You can register up to 10 peers.
- From [Protocol Setting] in [IPsec Setting], click [Create] and specify the protocol used for IPsec communication.
- Up to 10 protocols can be specified.
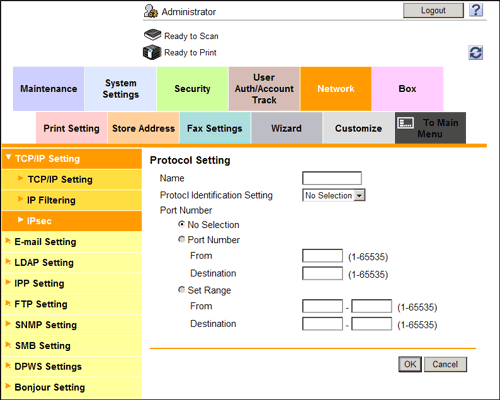
Settings Description [Name]Enter the protocol name (1 to 10 characters).[Protocol Identification Setting]Select a protocol used for IPsec communication.[Port Number]If [TCP] or [UDP] has been selected in [Protocol Identification Setting], specify the port number used for IPsec communication. - Up to 10 protocols can be specified.
- In the administrator mode, select [Network] - [TCP/IP Setting] - [IPsec] - [Enable IPsec], then click [OK].
- In [Enable IPsec], configure the following settings.
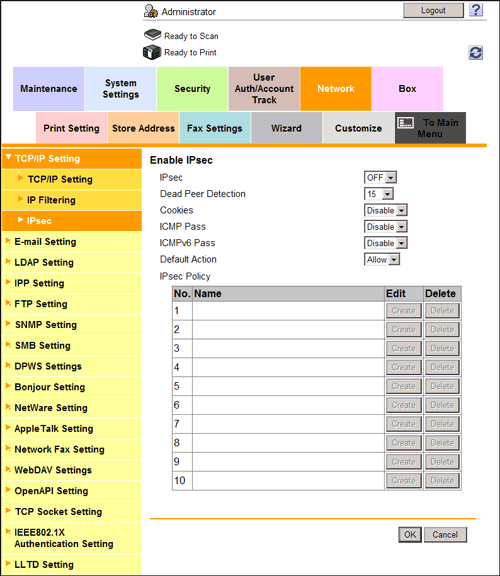
Settings Description [IPsec]Select [ON] to use the IPsec.[Dead Peer Detection]If no response can be confirmed from the peer in a certain period, the SA with the peer is deleted.Select a time that elapses before sending survival confirmation information to the peer how has not responded.[Cookies]Select whether to enable the defense using Cookies against denial-of-service attacks.[ICMP Pass]Select whether to apply IPsec to the Internet Control Message Protocol (ICMP).Select [Enable] to allow the ICMP packets to pass without applying IPsec to the ICMP.[ICMPv6 Pass]Select whether to apply IPsec to the Internet Control Message Protocol for IPv6 (ICMPv6).Select [Enable] to allow the ICMPv6 packets to pass without applying IPsec to the ICMPv6.[Default action]Select an action to be taken if no settings meet the [IPsec Policy] while IPsec communication is enabled.Select [Deny] to discard IP packets that do not meet the [IPsec Policy] settings. - From [IPsec Policy] in [Enable IPsec], click [Create], then configure the following settings.
- IP packet conditions can be specified to pass or allow the IP packets that meet each of the conditions.
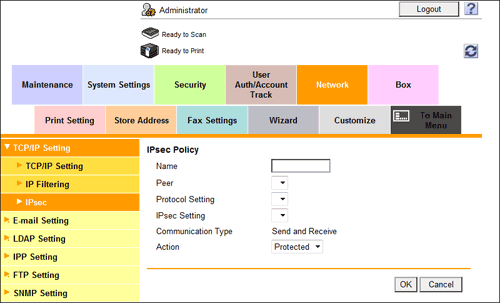
Settings Description [Name]Enter a name for the IPsec policy (1 to 10 characters).[Peer]Select a peer setting.Select the setting from those registered in [Peer] in [IPsec Setting].[Protocol Setting]Select a protocol.Select the setting from those registered in [Protocol Setting] in [IPsec Setting].[IPsec Setting]Select a peer setting.Select the setting from those registered in [SA] in [IPsec Setting].[Communication Type]Select a direction of IPsec communication.[Action]Select an action to be taken for the IP packets that met [Peer], [Protocol Setting], and [Communication Type].- [Protected]: Protect the IP packets that met the conditions.
- [Allow]: Do not protect the IP packets that met the conditions.
- [Deny]: Discard the IP packets that met the conditions.
- [Cancel]: Refuse the IP packets that met the conditions.
- IP packet conditions can be specified to pass or allow the IP packets that meet each of the conditions.